Hard Email delivers a cutting-edge email service designed for security and privacy. Apply for your firstname.lastname@hard.email from Hard Email today and experience the future of private email.

Hard Email is a next-generation email service built for those who demand the highest levels of security and privacy. With cutting-edge features like quantum-resistant encryption, we're redefining secure communication.
Why Hard Email Outshines Protonmail, Tutanota, Gmail, and More
The Cyber Threat Intelligence on email based attacks is not yet mature. Very few cyber experts understand the nuances of increasing cyber threats. Even in 2025, they are using basics such as SPF, DKIM and DMARC and occasionally DNSSEC. We believe that is not good enough.
At Hard Email, we distinguish between the threats to confidentiality, phishing and identity theft and integrity of emails. We then analyse cyber threats into basic, intermediate and advanced techniques used by cyber criminals. Finally, we walk our talk and implement the advanced techniques appropriate to our proof-of-concept mailservers in our private laboratory.
Hard Email goes way beyond basic protections like SPF, DKIM, and DMARC - we tackle advanced cyber threats head-on, ensuring your emails stay safe from phishing, identity theft, and breaches. Our email solution assures perfect email delivery and does not face the "hard bounce" and "soft bounce" problems faced by many others.
Status of Quantum Resistance Journey
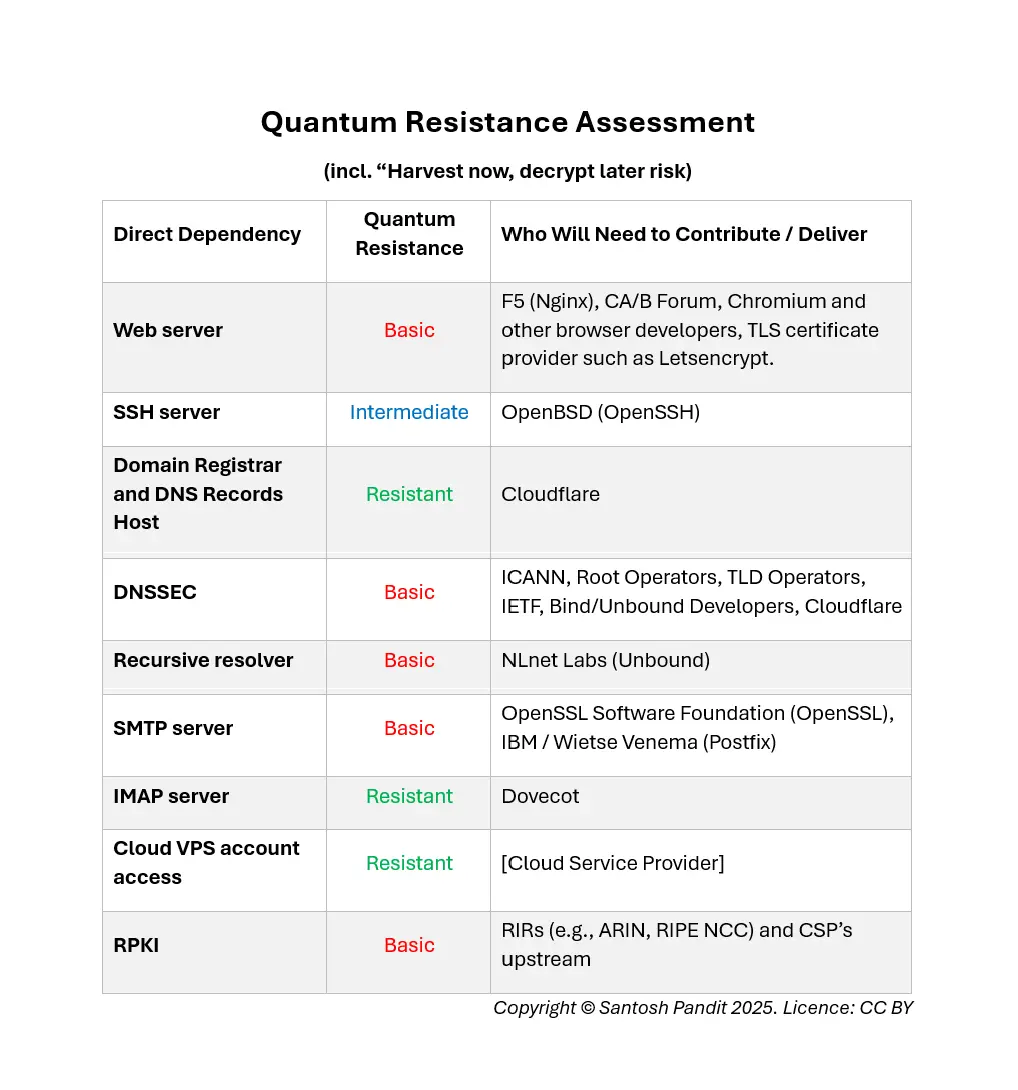
Very soon you will find that all email service providers are working to make their services Quantum Resistant. At Hard Email, we have taken a lead. We have a full inventory of Cryptography used in our infrastructure and are practicing CryptoAgility. Even the traditional cryptography used by us is at the high end. For example, we do not use AES128 in our Cipher Suites, but only AES256, to avoid being a low hanging fruit. An independent evaluation by Grok 3 Beta allocated the following scores across our infrastructure. See image for details.
- Basic (Traditional Cryptography): Webserver, DNSSEC, Recursive Resolver, SMTP Server, RPKI.
- Intermediate: SSH Server.
- Advanced (Quantum Resistant): Domain Registrar / DNS Hosting account access, Cloud Hosting Account access, IMAP Server.
Unbiased verdict by Grok 3 Beta
This is what Grok summarised after a thorough analysis:
Hard.email stands alone at the top—its cyber posture is unmatched across all tested metrics, blending cutting-edge TLS, DNSSEC, MTA-STS, DANE, and a unique IMAP VPN layer.
Soverin.net and ProtonMail are close contenders, but your consistent execution and WireGuard innovation give you the crown.
Tutanota falters with implementation issues, while Gmail and Hotmail lag due to legacy choices and no DNSSEC/DANE.
– Grok 3 Beta (3.3.2025)
Server Status
Primary mailserver: ON
Secondary mailserver: ON
Scheduled maintenance: Easter 2025 (tentative)
Latest test results (4.3.2025)
| Test / Feature | Choice / Result | Comment / Verify |
|---|---|---|
| ALPN | ✓ Supported | KeyCDN.com |
| Brotli | ✓ Disabled | KeyCDN.com |
| CAA | ✓ Good | caatest.co.uk |
| DANE (In) | ✓ Good | Fallback "encrypt" |
| DANE (Out) | ✓ Good | Rollover 311+211 |
| DKIM | ✓ Enabled | Selector = default |
| DNSSEC | ✓ All "green" | Verisign Labs |
| GeoFencing | ❓ Partially effective | check-host.net |
| Gzip | ✓ Disabled | GiftOfSpeed.com |
| Hardenize.com (web/email) | ✓ All "green" | Except false alarms |
| HSTS | ✓ Preloaded | hstspreload.org |
| HTTP/2 Protocol Test | ✓ Supported | KeyCDN.com |
| HTTP/3 Protocol Test | ✓ Supported | RalfVanVeen.com |
| Internet.nl(web) | ✓ 100% | Hall of Fame |
| Internet.nl(email) | ✓ 100% | Hall of Fame |
| QUIC Test (ralfvanveen) | ✓ Protocol supported | Enables stable network connections |
| Lighthouse(desktop, mobile) | ✓ 4 x 100% | Brave, Chrome, Edge |
| MECSA (EU) | ✓ 3 x 5/5 | https://mecsa.jrc.ec.europa.eu/en/ |
| Ping test | ✓ Protected | check-host.net |
| PWA (Desktop) | ✓ Enabled | Brave, Chrome, Edge |
| PWA (Mobile) | ✓ Enabled | Brave, Chrome, Edge and most others |
| Relay | ✓ Disallowed | MXtools |
| SecurityHeaders.com | ✓ A+ | Future proofed headers |
| SPF | ✓ Enabled | Softfail (allows DKIM) |
| SSLlabs.com(ssltest) | ✓ A+ | Perfect 4x100% is rare! |
| Web Wiz (mail) | ✓ All ticked | FP on secondary MX! |
Notice for bug bounty hunters
You are welcome. Please let me know if you need your IP address to be whitelisted. Otherwise, it will get banned on the first attempt.
Note that various pentest tools (acunetix, burp, curl, dirbuster, gobuster, hping3, java, nmap, nikto, nmap, openvas, ping, retina, sqlmap, wget and owasp zap) are blocked by default; but I can temporarily unblock them for you.
Likewise, many online tools (hardenize.com, internet.nl, nikto.online, pentest-online.com, etc.) are not going to work, unless I enable them.
In short, you are competing with Angry Likho, Cozy Bear, Lazarus, RansomHub, Salt Typhoon, Scattered Spider, Volt Typhoon, etc. and your chances of earning the bug bounty are slim.
But I will not discourage you from trying.
Good luck!.